As always we’ll start off with a nmap scan. As i always say this is the first step when doing any penetration testing since it will give you a pretty good idea of the services that are running on the box and sometimes you’ll find this services are vulnerable to some kind of attack that you can exploit and get a shell on the box
Youtube Walkthrough:-
Looking at the nmap result we see that three ports are open [FTP,SSH and HTTP]

I started by looking at FTP since it has anonymous login allowed meaning the user anonymous user can login to the box with any credential
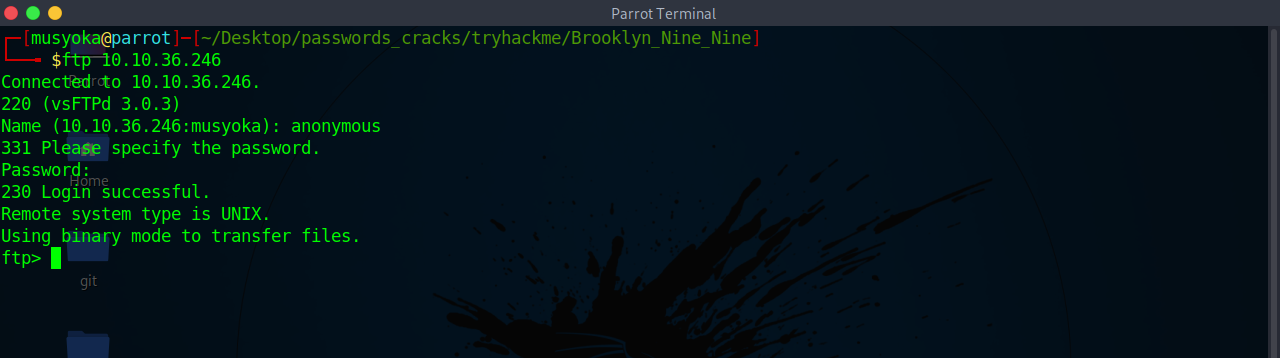
The password can be whatever you want. Doing a directory listing we get one file note_to_jake.txt
I would always recommend when doing a directory listing in FTP that you should always add -a flag
ls -aThis ensures that if there are hidden files you can also be able to view them

I downloaded the file to my local box and on viewing it we get some really useful information

First we get a bunch of usernames
1. Amy
2. Jake
3. Holtand with this username we can possible do a ssh bruteforce attack on the box
Next we also get some crucial information that point to the fact that Jake’s passwords might be weak.

And most weak password’s can be found in the rockyou wordlist. So we can leave a ssh bruteforce running in the background and continue to enumerate other ports which we haven’t looked at
The syntax to run ssh brutefore with hydra is as follows
hydra -l <username> -P <wordlist> ssh://<IP>
Next i decided to enumerate HTTP since it always has the biggest attack vector. On opening the webpage we just get a huge picture

Next i looked at the source code of the page and found a comment that gave us a hint on doing some stenography

So the next thing i did was to save the picture and try some common stenography checks on it
Exiftool didn’t give me much details except that maybe the server was build in 26th of June since that’s the file modification date

Steghide wasn’t able to extract any useful information since i didn’t have any correct passphrase or maybe there wasn’t any data to extract in the beginning

The next thing i could run was stegcracker to try and bruteforce the passphrase but i opted against it and left that idea as the last resort
I decided the next best thing i could do was to run gobuster which is a tool used to brute-force URIs including directories and files as well as DNS subdomains

While gobuster was running i decided to check is hyrda had found a valid login credentials
And as you see below hydra had found a valid credentials

Jake’s password was indeed really weak
jake:987654321I tried to login to the box using those credentials
And voila we are in

The next best thing we can do is run linpeas which is a bash script that find possible privilege escalation vectors and the colors it uses to output the results is really awesome
So i downloaded linpeas to the box using wget I’ve shown how it’s done in other walkthrough so am not going to do it again and after linpeas ran i found one really interesting thing
We could run less as any user on the box

Less which is a file pager (that is, a memory-efficient utility for displaying text one screenful at a time). Less has many more features than the basic pager “more”. If you’ve interacted with less more you probably know that you can execute a shell while you are using less by just passing the argument
!/bin/bashIf you didn’t know that you couls use a cheatsheet called GTFOBins
Just by searching less we get possible cheatsheet

I clicked on sudo and got the commands i was to run

The file to open doesn't necessarily have to be profile you can open any file
So i created a file called nano.txt and opened it with less

After i had opened the file i typed the command that will spawn a shell

Then pressed enter
And voila we had a root shell on the box

Now we can get both the user and root flag submit them and get our points

And the box is done.
The second way to get root on the box was also simple let’s jump right in and see how it is done
Looking at Holt’s home directory we see that he has the user flag

And since we could run sudo command as any user i decided to run less as the user hold and get a shell as him
The command i used was
sudo -u holt less ../jake/nano.txtThe -u flag tell sudo to run the command as that specific user
After i opened the file i opened the file i executed the same command to give me a shell as Holt
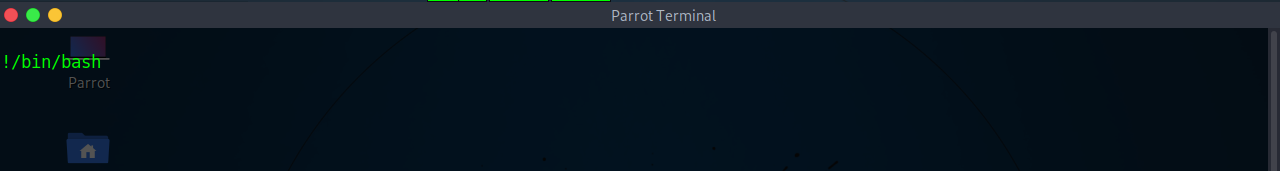
After i pressed enter i got a shell as the holt

Running sudo -l again we see that we can ran nano as any user even root without having the right credentials

And also when you are in nano you can execute a command to give you root. The cheat sheet is also available in GTFOBins

Clicking on sudo we are provided with the commands we can run

1. We open nano as root
2. press CTRL + r followed by CTRL + xAnd nano opens up a textbox that can be used to execute commands

3. we run the command ----> reset; sh 1>&0 2>&0
After pressing enter we should get a root shell but it never worked

The screen just hanged but I’ll revert the box try it again and see if it works if it does I’ll update the writeup but that’s it for now guys till next take care
After hours of trying to figure out what the problem was i never found an answer. But i started asking myself what else can we do with a text editor that’s running as root????
- We could read files belonging to root so let’s try reading root.txt

And as seen below we got the contents of the root flag

Since we could read files owned by root what about we try reading the shadow file
Shadow file contains a list of hashes for every user on the the box. Those hashes we could try to crack and see if we can get the root’s password


Looking at the shadow file we see that it’s blank we just have the hashes for the other user of which even if we crack we will not be able to get root access to the system so i opted against trying to crack those hashes so that’s a dead end
What else could we do on the system?????
Since we have root privileges when running nano we could edit the /etc/passwd and add a user with root privileges on the system
Let’s see how this will work
First we’ll need to create a password hash with openssl
The command that i used is as below
openssl passwd -1 musyoka
I’ve successfully generated a MD5 hash password for the word musyoka. This hash will be added in /etc/passwd
2. Lets create a new user in /etc/passwd
As seen below I’ve created a new user called musyoka in /etc/passwd file and I’ve added the hash i generated to that user in the passwd file

Now i saved the file and tried to login as musyoka in the box

After typing the password musyoka i got a root shell !!!!





































Comments
Post a Comment