Youtube Walkthrough :-
As always we’ll start off with a nmap scan

And we get only two ports are open and what’s weird is that there is no web server. So i decided to expand my nmap scope scan by doing a full TCP scan maybe we missed some open ports that might have easily exploitable services
And we get two more ports are open the standard SMB ports
So i decided to analyze the output of nmap maybe we might be lucky and find an exploitable service
I decided to do a searchsploit on the ftp and all the vulnerable versions are 2.*. But we get a really sensitive information that can help us exploit the box . we find that anonymous ftp login is allowed. Just by using the username anonymous and the password doesn’t matter we are able to log into the box also the ftp is writable this is seen from nmap

So i decided to see what files might be present on the ftp share maybe we might get lucky and find some credentials lying around

i downloaded all the files to my box and examined them
- To_do.txt just a reminder that the owner of the box need to disable anonymous login

2. Clean.sh is a bash script that delete file that are in /tmp directory

3. removed_files.log is a log file showing if files were remove from /tmp directory

But we didn’t have a way to execute the bash script and it seemed like a dead end so i decided to enumerate the SMB share
And we get a SMB share called pics

Since NULL authentication is allowed i logged into the share

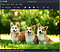
I decided to view them and they were just images of puppies


My first though was it must be a stenography challenge but got nothing from them so i hit a dead end
Looking back at my enumeration i remembered the ftp files were writable and there was a script that was being executes somehow we don’t know how till now. I decided to download the log file a second time and see if the logs had increased and voila we find that the lines in the log files had increased meaning probably there was a cron running that was executing the script and since we can write to the script why not add a malicious bash reverse shell line that will give us a shell on the box once the cron executes the script

I edited the clean.sh script and added a bash reverse shell line with my IPAddress

Now i again logged into ftp and tried to find a way to add that code to the clean.sh script
And using the help command we find append that can allow us to append a file

And i successfully appended my edited bash script to the one in ftp direcory

Then i created a listener on my box using netcat and all i had to do was wait for a callback
And after a few second a got a callback to the box we have a shell

And we have the user flag

Now i looked in the passwd file to see other users that are in the box
And we get only two users have a shell on the box root and namelessone

Now we had to escalate out privileges to root. I decided to run linpeas which is a Linux local Privilege Escalation Awesome (You can find it from the link provided)Script that will automatically identify any possible privilege escalation vectors. I hosted a web server on my local box and downloaded the script to the compromised box

And then i executed it
And we see we are a member of sudo and adm group
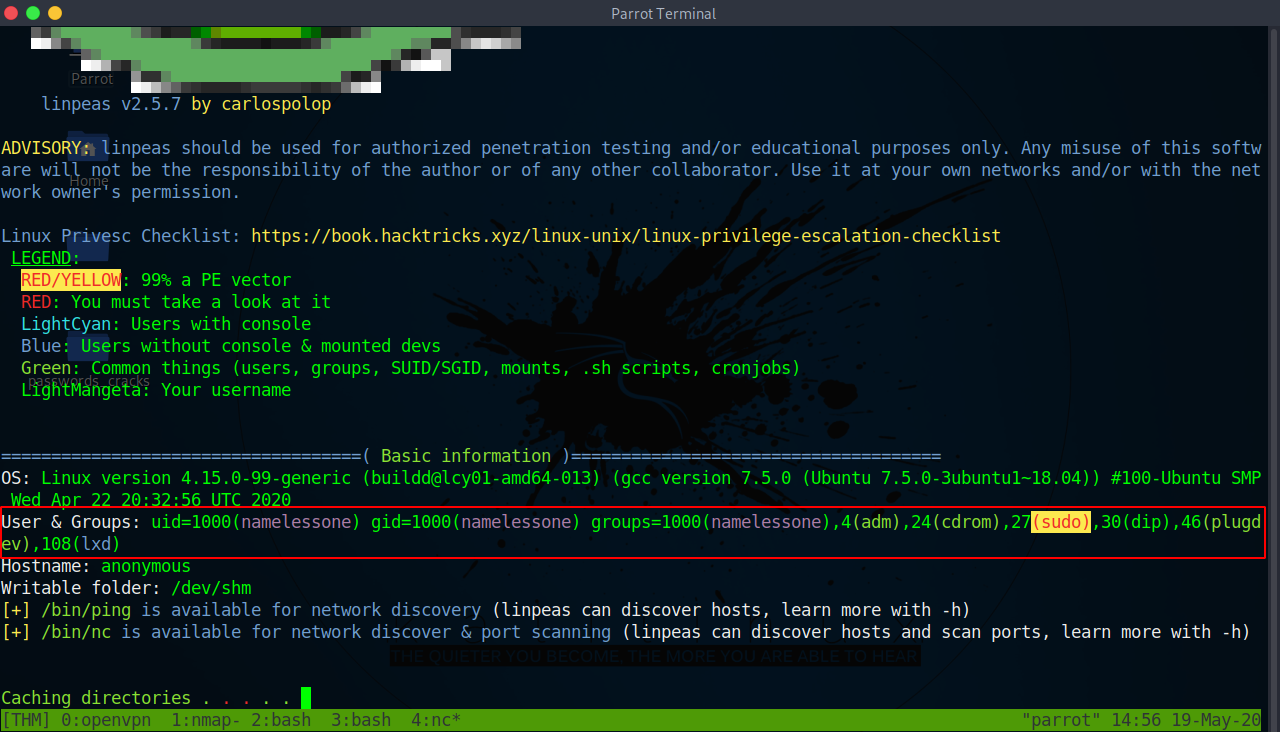
Meaning if we had the password for namelessone we could just escalate to root by using sudo command
So my first through was that probably we had to find a credential that was left somewhere in the box but it was a dead end
While i was going through the output of linpeas i found some directory that indicate the privilege escalation might be through lxd. Since we are in the sudo group we can exploit it to gain root priviledge on the box

LXD is Ubuntu’s container manager utilizing Linux containers. It could be considered to act in the same sphere as docker,
The lxd group should be considered harmful in the same way the docker group is. Under no circumstances should a user in a local container be given access to the lxd group. This is because it’s entirely trivial to exploit.
First i’ll download lxd alpine builder from GitHub because we need an image but Ubuntu image is really big and due to this we’ll build our own Linux image which has a small size in our local box and then copy to the vulnerable box

- -a specifies the architecture that want to build a 32 bit image
After it finishes building you should you should have a alpine gzip compressed data

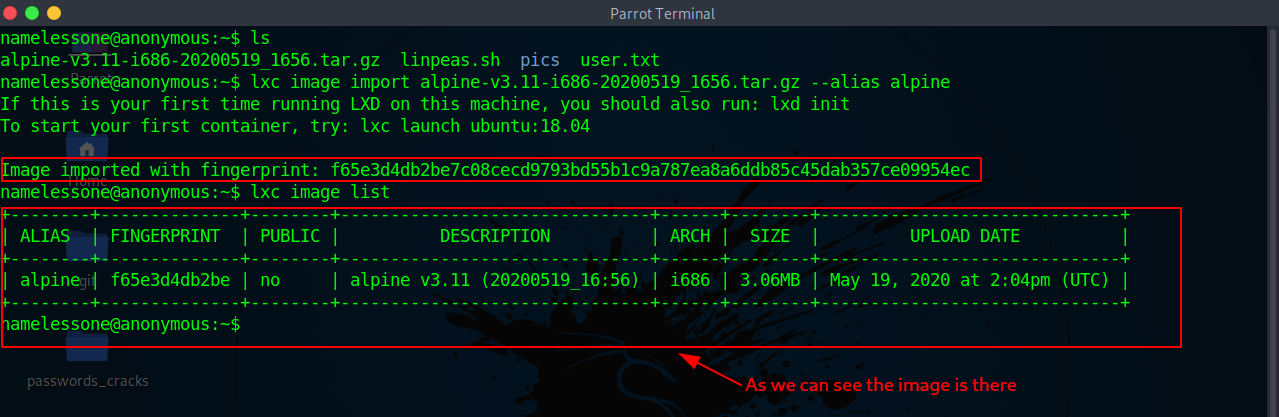
Now we upload that image to the target machine

Next we import the image to lxc
Now we create the container

If you get the error above you need to use the configuration below

Then try the command again

And voila we have successfully created the container
Now we can list the device

Next we hard a storage device to this device

Now we initialize the device and execute it
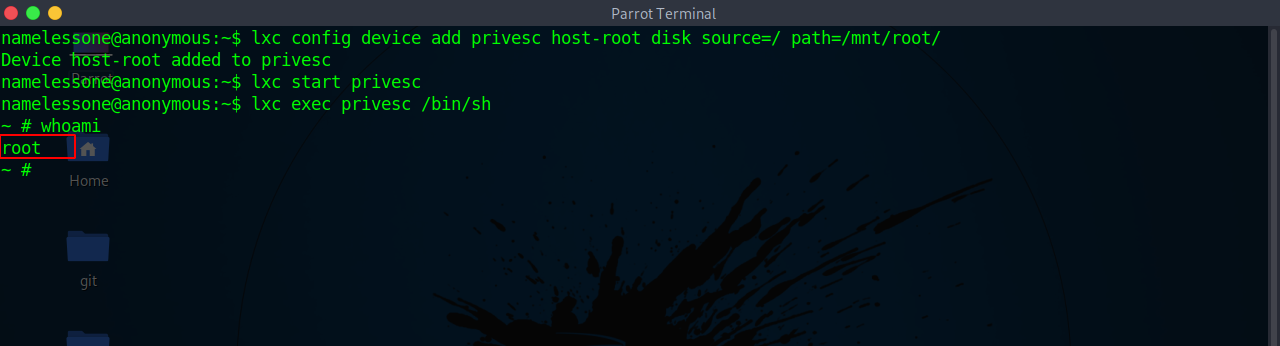
And we are root on the box

We can now submit the flag and get the points


























Comments
Post a Comment