
Lian yu is a beginner level room on Tryhackme based on the TV serial.
This machine requires a lot of fuzzing, steganography, and privilege escalation.
Youtube Walkthrough:-
Webserver
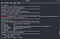
The first question on tryhackme was about the webserver so I run the Gobuster against the website

So I found a directory after and the source code reavled the following:

We see a comment It looks like a keyword or name we will use it later.
Now we run the Gobuster against the directory we found

And we found a subdirectory

After viewing the source page we got some hint of extension we can use gobuster to find file name with this extension by using -x parameter, which lets us search file extension.

When we searched the file with .ticket extension we found a file let’s see what it is.

We got some characters but it is encoded by the hint of tryhackme we can decode this using CyberChef

The string was encrypted in Base-58. You can check the encoding type through magic module present in Cyberchef
We have already founded a username v******e .
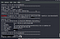
We can try login into FTP

Ok, so we are in. We can see there are 3 image files we can download all files using get command
After downloading files, one image named as “Leave me alone*
So we used exiftool to check the image.

We got some Error in the image from Exiftool. This means image’s header might be corrupted, we can google the Hex table of PNG image to check values and also modify the image with Hexeditor.
We searched at google and find the PNG image correct values

After we run Hexeditor with the PNG image file

The values of the hex header PNG image are not matching so we have to modify the values and save it.

After saving we can again verify with ExifTool

The Error has been gone
Now, let’s try to open the image

It’s says the thing we want is pa****** .The other two images may also contain some useful information let’s check them.

Its telling that it contains a zip file
When we use the password which we got from the image I’m able to get the zip file
Lets unzip the zip file
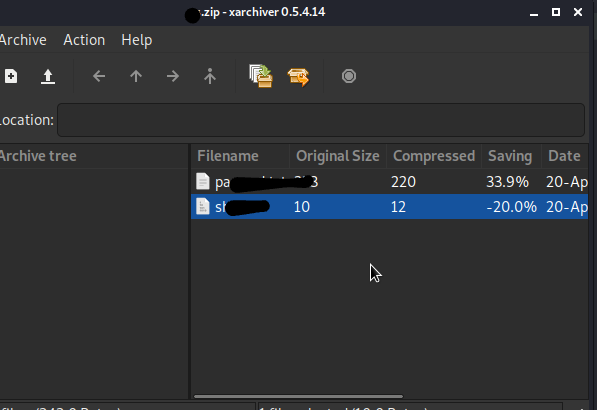
File pa****** contains some info and another file s*** contain the password of SSH but we don’t know the Username we can check the FTP directories to get some information

We got a new username. Now, we can SSH into system

Now you can do “ls-la” and “cat user.txt” to get user flag
After getting user flag for privilege escalation, let’s see what permissions do the New user have
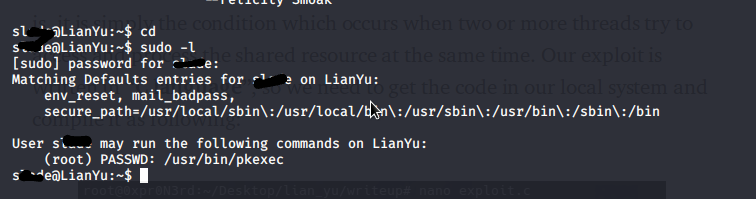
Looks like we can run “pkexec” with root privileges.
I saw the manual page of pkexec by typing “man pkexec” in the terminal and it tells us that pkexec allows an authorized user to execute the program as another user and if the user is not specified that it runs the program as root.
So now, we are going to run “/bin/bash” program as root to get root access.

Now, we have the root access and we can do “ cat root.txt” to get root flag.








Comments
Post a Comment